Navigating the Digital Battlefield: Understanding Internet Attack Maps
Related Articles: Navigating the Digital Battlefield: Understanding Internet Attack Maps
Introduction
With great pleasure, we will explore the intriguing topic related to Navigating the Digital Battlefield: Understanding Internet Attack Maps. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Digital Battlefield: Understanding Internet Attack Maps

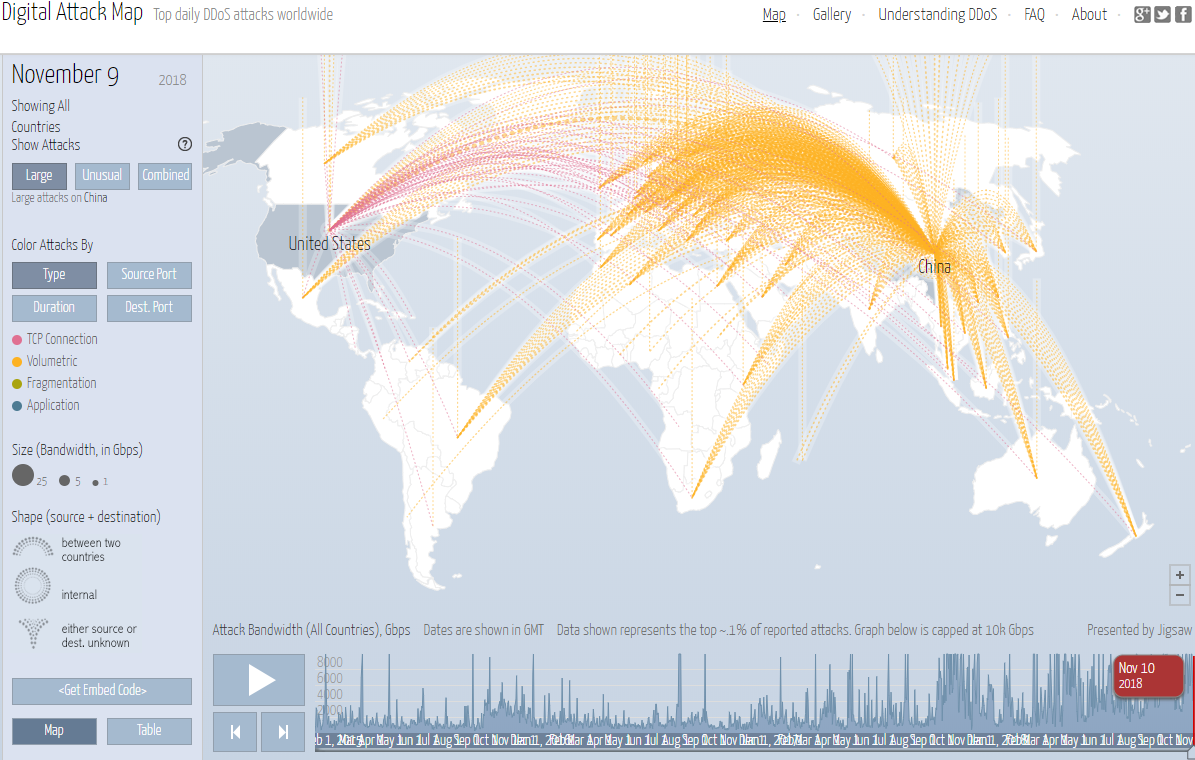
The internet, a vast and interconnected network, is not a utopia free from danger. It is, in fact, a digital battlefield, where malicious actors constantly seek to exploit vulnerabilities and disrupt operations. To comprehend the scope and nature of these threats, security professionals and organizations rely on a crucial tool: internet attack maps.
These maps, often presented as interactive visualizations, offer a real-time or near-real-time view of cyberattacks globally. They provide valuable insights into the geographic distribution of attacks, their targets, the types of attacks, and the actors involved. Understanding this dynamic landscape is essential for proactive defense and informed decision-making in the face of evolving cyber threats.
Decoding the Landscape: Unveiling the Layers of an Internet Attack Map
Internet attack maps typically present a comprehensive overview of cyber threats, encompassing various elements:
- Geographic Distribution: The maps depict the origin of attacks, highlighting regions with high attack activity. This information helps organizations identify potential threats based on their geographic location and understand regional trends.
- Target Types: Attack maps often categorize targets, showcasing attacks aimed at specific industries, sectors, or even individual organizations. This granular view allows businesses to assess their vulnerability based on their industry and understand the specific threats they face.
- Attack Types: Maps categorize attacks by type, including DDoS attacks, malware infections, phishing campaigns, and data breaches. This categorization helps organizations prioritize their security efforts based on the most prevalent threats.
- Attack Vectors: Attack maps often detail the methods used to launch attacks, such as compromised websites, phishing emails, or vulnerabilities in software. This information helps organizations identify potential entry points for attackers and implement targeted security measures.
- Attacker Groups: Some maps identify the groups or individuals responsible for specific attacks, providing valuable insights into the motives and capabilities of attackers. This information helps organizations understand the threat landscape and develop countermeasures.
Beyond Visualization: The Power of Data and Analysis
While visually appealing, internet attack maps are more than just pretty pictures. Their true value lies in the data they collect and the insights they provide. By analyzing the data presented on these maps, organizations can gain a deeper understanding of the evolving cyber threat landscape. This analysis can be used to:
- Identify Emerging Threats: Analyzing trends in attack types, targets, and geographic distribution helps organizations anticipate and prepare for emerging threats.
- Prioritize Security Efforts: By understanding the most prevalent threats, organizations can prioritize their security investments and focus on mitigating the most likely risks.
- Improve Incident Response: Attack maps provide valuable context for incident response teams, helping them understand the nature of the attack, its potential impact, and the necessary steps to mitigate the damage.
- Enhance Risk Management: By analyzing attack data, organizations can better assess their overall risk profile and develop comprehensive risk management strategies.
- Inform Strategic Decision-Making: Attack maps provide critical information for decision-makers, enabling them to make informed choices about resource allocation, security investments, and overall cybersecurity strategy.
Navigating the Map: A Guide to Effective Use
While internet attack maps provide valuable insights, it is crucial to use them effectively. Here are some tips for maximizing their benefit:
- Choose the Right Map: Not all attack maps are created equal. Select a map that provides the most relevant data for your organization, considering your industry, geographic location, and specific security concerns.
- Understand the Data: Familiarize yourself with the data presented on the map, including the methodology used to collect it, the time frame covered, and the limitations of the data.
- Analyze Trends: Look for patterns and trends in attack data, identifying emerging threats, popular attack vectors, and the most targeted industries.
- Integrate with Other Data: Combine the insights from attack maps with other security data, such as threat intelligence feeds, vulnerability reports, and incident logs, for a more comprehensive view of your security posture.
- Use the Information Proactively: Don’t just passively observe the data; use it to proactively strengthen your security posture, implement preventative measures, and prepare for potential attacks.
Frequently Asked Questions about Internet Attack Maps
Q: Are internet attack maps real-time?
A: While some maps claim to be real-time, most provide near-real-time data, with updates occurring at regular intervals. The frequency of updates can vary depending on the map provider and the data sources used.
Q: How accurate are internet attack maps?
A: The accuracy of attack maps depends on the data sources, the methodology used to collect and analyze the data, and the timeliness of updates. It is important to note that not all attacks are reported, and some data may be incomplete or inaccurate.
Q: Who uses internet attack maps?
A: Internet attack maps are valuable tools for a wide range of users, including:
- Security Professionals: Security analysts, threat intelligence teams, and incident response teams use maps to monitor threats, identify emerging trends, and make informed decisions.
- Businesses: Organizations use attack maps to assess their risk, prioritize security investments, and develop proactive security measures.
- Government Agencies: Government agencies use maps to track national security threats, understand cybercrime trends, and develop national cybersecurity strategies.
- Researchers: Researchers use attack maps to study cybercrime patterns, analyze attacker behavior, and develop new security technologies.
Q: Are internet attack maps publicly available?
A: Yes, many internet attack maps are publicly available, often provided by security vendors, research organizations, or government agencies. These maps typically offer a free, basic level of access, with more detailed information available through paid subscriptions.
Conclusion: Navigating the Digital Landscape with Knowledge
Internet attack maps are a vital tool for navigating the complex and ever-evolving cyber threat landscape. By providing a visual representation of attack activity and offering valuable data insights, they empower organizations to make informed security decisions, prioritize their defenses, and prepare for potential attacks.
Understanding the data presented on these maps, analyzing trends, and integrating them with other security information are essential for effectively utilizing this powerful tool. As cyber threats continue to evolve, internet attack maps will remain crucial for organizations seeking to protect their data, systems, and reputation in the digital world.






Closure
Thus, we hope this article has provided valuable insights into Navigating the Digital Battlefield: Understanding Internet Attack Maps. We thank you for taking the time to read this article. See you in our next article!